Guides and reports
Choosing between end-to-end encryption or point-to-point encryption
We look at the differences between end-to-end encryption (E2EE) and point-to-point encryption (P2PE) to help you decide what's right for your business

If you’re a child of the nineties or earlier, you’ll remember your local corner shop, general store or newspaper stand being cash or check only, with paper receipts (only when requested), and special ink pens to test if the bills you were handing over were forgeries.
The world has changed a bit since those halcyon days of the handwritten signature being the height of risk protection, and today risk management tools are constantly evolving to keep up with new types of fraud and data attacks.
Encryption is now a legal requirement. And since P2PE was developed back in 2012 the world of in-person payments has evolved even further, and so too has the way traditional payment value chains operate.
These changes offer a more simplified way for retailers to encrypt payments data while meeting their PCI compliance obligations. So let’s get into the details of our E2EE, P2PE, and the differences between the two.
E2EE and P2PE: The basics
End-to-end encryption is the process of encrypting payments data for the entirety of the payment process and is Adyen’s default way of protecting in-store payments. With our E2EE, cardholder data never leaves the Adyen environment, meaning that from when the card is inserted or tapped at the point of sale terminal, cardholder data is encrypted by Adyen and only ever touched by Adyen. This is because we manage the entire payments value chain. It allows us to better protect your data, and give you a greater level of assurance that cardholder data cannot be accessed.
P2PE is a type of encryption that was developed by the Payment Card Industry Security Standards Council (PCI SSC). It offers protection for terminals and card-present transactions against device tampering and data breaches.
We offer both types of encryption.
What are the differences?
There are three key ways that our E2EE and P2PE differ:
One partner


Using our E2EE means we’re your sole payments partner. We’re your gateway, processor, and acquirer rolled into one. With P2PE, encryption is often carried out between different providers.
Every merchant needs to prove to their acquirer that they process online and in-store payments securely. Since we act as an acquirer for our merchants, they’re required to report on their PCI compliance to us with something called an SAQ.
The Self Assessment Questionnaire (SAQ)
To meet PCI compliance, businesses must complete a questionnaire, also known as an SAQ.
For E2EE
Using our E2EE means you only have to complete the SAQ B-IP, which is relatively straightforward. And as your acquirer, we only ask you to complete two of the requirements, 22 simple questions.
Example questions include:
- The make and model of the device
- Location of device (for example, the address of the site or facility where the device is located)
- Device serial number or another method of unique identification
For P2PE
Businesses need to complete a different SAQ. It has three requirements and 35 questions.
Example questions include:
- Are data storage amount and retention time-limited to that required for legal, regulatory, and/or business requirements? (Review data retention and disposal policies and procedures. Interview personnel (b) Are there defined processes in place for security?)
- Is there a quarterly process for identifying and securely deleting stored cardholder data that exceeds defined retention requirements?
- Are all media physically secured (including but not limited to computers, removable electronic media, paper receipts, paper reports, and faxes)?
The physical security of point of sale terminals
P2PE requires the following checks from a document called the P2PE Instruction Manual (PIM), provided to merchants by their solution provider, to assist them in remaining PCI compliant:
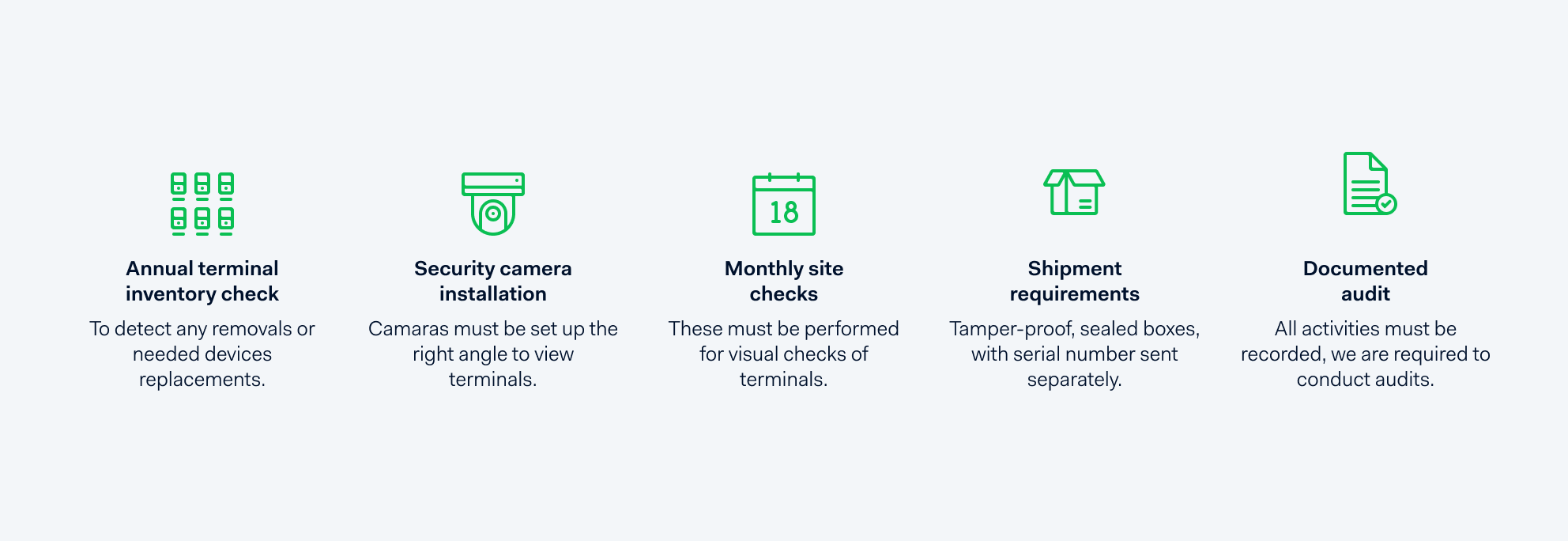
Adyen’s handling of terminals is similarly secure, regardless of whether or not the merchant chooses to use P2PE. With E2EE we don’t require any of the above. The only item you’ll see is the tamper-proof, sealed boxes we send our terminals in.
With P2PE, staff must record these actions precisely per the PIM. After that, the acquirer is required by the PCI SSC to audit these records yearly. This is where businesses sometimes miss the mark when seeking PCI compliance.
What’s the right solution for my company?
It comes down to the level of security you need as well as how you and your business manage your resources.
E2EE
We believe in high-quality data security, without all the extra work. This is why we built an E2EE payment solution in a way that ensures the best possible data security.
More agile, decentralized businesses may find our E2EE more efficient. Examples of these could be enterprises who don’t need to centralize operational control, such as franchises, or scale-ups with smaller teams and aggressive roadmaps.
P2PE
Larger, more heavily-resourced businesses with an aversion to risk prefer the P2PE solution as it gives them an added layer of control around the physical handling of terminals.
They’re likely willing to pay per POS terminal for the added security it provides. They will also spend more time and human resources to maintain the PIM.
If you have E2EE, why is Adyen offering P2PE?
We build to benefit all of our merchants (not just one). So if there is a solution out there that’s secure, validated, and people trust, we want to make sure we can offer it to you. By using P2PE with us you still benefit from working with a single partner.
With that being said, we firmly believe in the virtues of our end-to-end solution.
If you have any questions about E2EE, P2PE, orrisk, please get in touch